SDP model supersedes VPN solutions

The Internet of Things (IoT) remains a relatively young technological innovation, although the concept of “communicating devices” is a well-established and accepted paradigm in virtually all industries. In fact, estimates by many experts predict that there will be between 20 and 30 billion IoT devices by 2021, with an industry value of $520 billion.
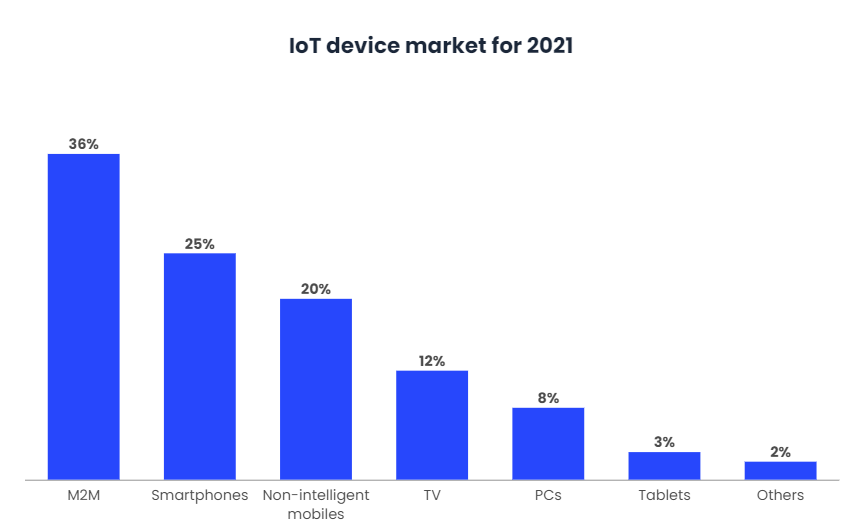
To communicate, move, share, process and leverage the data each of these devices is generating, each company must be connected to clouds and edge gateways across IP networks. With use cases spanning virtually every industry in the world, the possibilities for your applications are endless. Unfortunately, so are their cybersecurity vulnerabilities.
As a result, IoT security remains the main stumbling block on the road to adopting connected devices. This is because IoT devices are commonly deployed outside an organization’s traditional business boundaries. This means that protecting the devices and their associated data is particularly challenging.
The challenge lies in the fact that these endpoints are designed for light data transmissions, not enterprise-class security protocols. Faced with this situation, Software Defined Perimeters (SDP) have been gaining ground in the IoT area for good reason.
Software defined perimeter
The Software Defined Perimeter (SDP) is an emerging security model that has a set of specific characteristics defined by the nonprofit Cloud Security Alliance (CSA). It is defined primarily by two important characteristics:
- The two ends of the connection must be authorized before traffic can pass between them.
- SDPs essentially hide devices and traffic from the public Internet, even while using it as a transport mechanism.
In a typical SDP architecture, there are several points where each and every connection is validated and inspected to help demonstrate authenticity and limit the risk of attack. Typically, in the SDP model, there is a controller that defines the policies by which clients can connect and gain access to different resources.
The gateway component helps direct traffic to the right data center or cloud resources. Finally, the devices and services make use of an SDP client that connects and requests access from the controller to the resources.
The dangers are real
The value and efficiency of IoT implementations are based on equipping as many devices as possible, as quickly as possible, with distributed configurations for fast data transmissions that provide real-time information. Costs would increase rapidly if organizations had to equip each endpoint device with the most expensive hardware capabilities, which in turn would limit the ability to distribute these devices and, consequently, the tracking value they would produce.
The ability to enjoy discrete data transmission as isolation is an inherent benefit of SDP. In other words, SDP overcomes the limited cybersecurity capabilities of endpoint devices and the fact that they are outside typical perimeter defenses. In addition, the SDP can enhance the overall security of distributed networks by strengthening both ends: edge computing devices and gateways, and public and private centralized clouds.
It is challenging to determine which aspect of IoT security is most inhibiting: the fact that transmissions originate outside the conventional boundaries of enterprise cyber security or that the devices are not designed for modern security challenges.
The reality is that even if devices are behind traditional cyber-security perimeter defenses, such as virtual private networks (VPNs) or firewalls, the growing number of data breaches indicates that they would be just as vulnerable.
Types of attacks mitigated by SDP
Fortunately, the SDP protects businesses from a wide range of threats and piracy techniques that criminals take advantage of to attack the corporate network.
- Man in the Middle (MITM)
A MITM is a type of security breach in which the author positions himself in a conversation between a user and an application, either to spy on or supplant one of the parties, making it look like a normal exchange of information.
Both SDP and VPN solutions can provide protection against MiTM attacks by sending network traffic through an encrypted tunnel. However, SDPs ensure always-on implementation that protects web traffic and secures access to the enterprise network.
Many conventional VPN solutions use a split tunnel to send web traffic directly to save costs and reduce latency, leaving endpoints vulnerable. SDPs, on the other hand, secure open endpoints to address this problem.
- DNS hijacking
DNS hijacking is another danger when working on public WiFi networks. Hackers can intervene in DNS resolution to redirect people to a malicious site instead of the one they were trying to reach.
Once the individual has control of the DNS, he can direct others accessing it to a web page that looks the same but contains additional content, such as advertisements. They can also direct users to pages that contain malware or a third-party search engine.
Always-on SDP solution based on a network architecture as a service uses a protected and secure DNS service to perform resolution and protect against DNS hijacking.
- SSL Removal
SSL removal is a type of MiTM attack that degrades communications between the endpoint and the server to an unencrypted format in order to read the content. One way to avoid removing SSL is to install HTTPS Everywhere, a browser extension that applies HTTPS communication whenever possible, preventing an uninvited party from reducing communications to HTTP. SDPs also prevent such threats, mitigating them by sending all traffic through an encrypted tunnel.
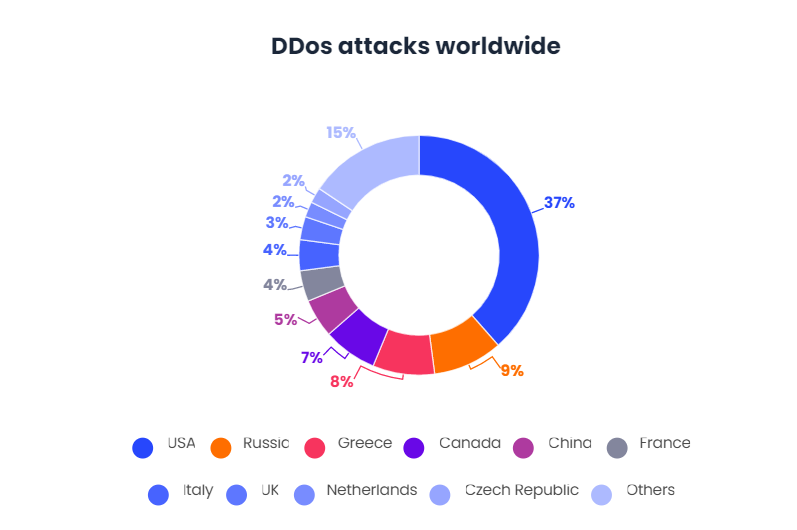
- Attack DDoS
There are two general forms of DoS attacks: those that block services and those that flood services. SDP solutions can prevent any type of DDoS attack by protecting the application instead of the end user’s device. In the SDP model, applications (and the infrastructure that hosts them) are not directly connected to the Internet. The SDP solution acts as a gateway that prevents permission for any unauthorized access.
- Port Scanning
Hackers use port scanning to locate an open port on a network that can be exploited for an attack. There are two main concerns related to port scanning that security administrators should be aware of.
- The security and stability issues associated with open ports and the program responsible for delivering the service.
- Security and stability issues associated with the operating system running on the host through open or closed ports.
Because SDP solutions isolate all network resources from the Internet, cybercriminals cannot take advantage of this technique to find a way to log in.
- Problematic exploits
Like BlueKeep, which recently made headlines, worms are exploits that pass from one machine to another. Conventional endpoint security platforms, such as antivirus and EDR, can’t prevent this type of exploit, and user awareness training won’t help either.
Since no user action is required, the simple act of connecting a user’s laptop or phone to a network while an infected device is connected to the same network is sufficient. Because worms move across a network, in most scenarios, an enterprise firewall or VPN cannot mitigate an exploit like BlueKeep.
On the other hand, a zero-trusted SDP provides users with a single, fixed identity and microsegmented access to only the resources they need for any infected device to have very little impact on the network as a whole.
- Brute force attacks
Like DDoS, a brute force attack is one in which the hacker attempts to gain access to a network or application through repeated login attempts. An SDP solution will immediately detect failed access attempts, but will also notice suspicious geolocations or times of day, changes in device posture and lack of active antivirus and deny access.
- Legacy Applications
Many legacy applications are designed to be accessible from the Internet and lack the basic security that is taken for granted in modern software-as-a-service (SaaS) applications, for example. Restricting access to legacy applications through an SDP solution isolates the application from the enterprise network and the Internet and adds adaptive controls to reduce risk.
Software Defined Perimeters secure gateways at the application layer. With sufficient encryption capabilities to ensure that third party application vendors do not have access to communications, SDPs promise a highly defended perimeter that is ideal for organizations exchanging information through the cloud.
What does an SDP model offer?
Parallel to the security presented by an SDP model in the face of a cyber attack, the advantages of this approach are considerable: discrete data transmissions, microtunnels take advantage of an improved UDP for security, and the generation of random ports makes it difficult to open ports. If it really stands out for something, it’s the commercial value that awaits.
Isolation of a network enabled by this method ensures that there are separate transmissions for payments, reward programs, and monitoring, which greatly mitigates the possibility of distributed denial-of-service and lateral motion attacks that can compromise the IoT network.
The SDP can operate in a variety of scenarios, depending on the types of devices and how they are connected. Six scenarios are defined in the current version of the SDP v2.0 specification:
- Customer to Gateway
- Client to Server
- Server to Server
- From client to server to client
- From customer to gateway to customer
- Gateway to gateway.
The client is usually the end user’s device (laptop, tablet, smartphone, or IoT device) that runs the SDP software. A gateway is a system that provides authorized users and devices with access to protected processes and services. The gateway can also trigger monitoring, logging, and reporting on these connections.
Typically, the gateway serves as an interface for systems that do not run the SDP software natively. The server is a system that provides the desired services to the client, but runs the SDP gateway software. Basically, the difference between a gateway and a server is that the gateway provides independent SDP functionality, while the server includes the SDP software within the server itself.
Convincing for any case of IoT use
Regardless of the industry, it is critical to understand that an SDP approach provides these same cybersecurity benefits of hidden data transmissions for any IoT use. For example, the security benefits that could be seen in a financial services organization are obvious, the integral value of this approach not only secures data coming from IoT devices to the cloud, but also helps to stabilize the overall networks that support any operation.
SDPs allow organizations to provide reliable cyber-protection in a way that is light enough for endpoint devices and optimal for data transmissions from remote locations. Proper implementation of this approach reinforces the line of commercial advantages for which IoT is hailed, while stabilizing data transmissions from the networks of organizations in general. This approach can make a critical difference in making IoT projections a concrete reality.
According to CSA information, most organizations still do not understand the importance of the Software Defined Perimeter. And within the percentage of those who do, they primarily use it as a replacement for network access control and VPNs. However, the main obstacle to adoption, according to the CSA, is the lack of technical details for SDP implementation.
Conclusions
There really isn’t an industry where IoT can’t be present. It’s a growing business. As stated at the beginning, the IoT market value is expected to reach approximately 520 billion dollars by 2021, more than double, compared to 235 billion dollars in 2017. That’s why it’s important to understand the need to secure devices.
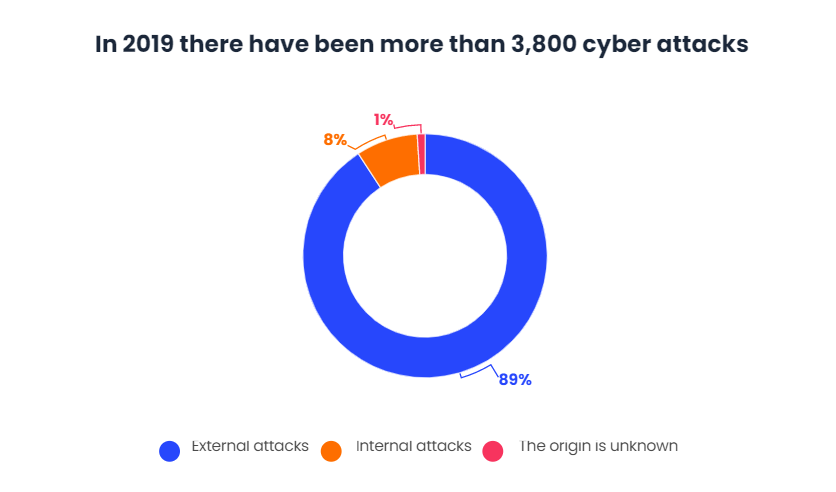
Initially, organizations must address the basic cybersecurity issues that impede their progress. This is not a disproportionate concern because during the first six months of 2019 alone, there were a total of 3,813 security breaches, or approximately 20 per day.
Against this backdrop, the SDP allows organizations to provide reliable cyber security in a manner light enough for endpoint devices and optimal for data transmissions from remote locations. The ideal implementation of this method reinforces the line of commercial advantages for which IoT is hailed, while stabilizing data transmissions from organizations’ networks in general. This approach can make a critical difference in making IoT projections a concrete reality.


