Protecting a company through Bug Bounty Platforms

Bug Bounty Platforms (BBP), or bug bounty platforms, were born to shape a new era of cybersecurity. These programmes allow hackers to report bugs in an organisation’s system, such as security exploits, process problems, hardware failures and various vulnerabilities. Finding vulnerabilities allows for increased metrics and new programmes to embrace new challenges and experiences.
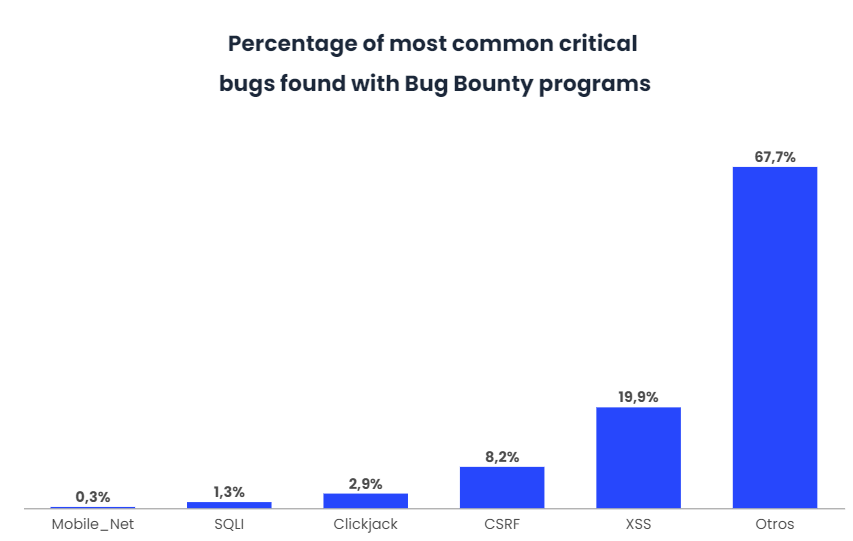
In essence, it is a compensation system offered by many websites, organisations and software developers, whereby individuals can receive recognition and rewards for reporting bugs in different companies’ systems. In recent times, more and more companies are joining bug bounty platforms.
Bug Bounty programmes
These programmes have been around for more than two decades, but they suffered from limitations and there was a need for middleware in the cybersecurity market. Bug Bounty platforms must respect the security policy of each website, deliver high quality reports and provide any relevant information. Among the most prominent programmes in 2021 are Hackerone, BugCrowd, OpenBugBounty, SynAck and YesWeHack.
All of these platforms have decided to start their transformation from security testing to all-in-one cybersecurity platforms, i.e. offering classic penetration testing alongside other services.
- Hackerone
Hackerone is the industry leader. There are two ways to use this platform: firstly, use it to compile vulnerability reports and then the company itself takes care of their resolution or, secondly, let the platform’s developers compile these vulnerability reports, verify them and contact hackers for resolution.
This platform is used by large companies such as Google Play, GitHub or Starbucks. It is also known for hosting the US government’s Bug Bounty programmes, including the Department of Defense’s vulnerability disclosure programmes.
Hackerone now offers penetration testing services, making it a much more comprehensive platform. It has an established place in the industry with extensive security certifications, such as ISO 27001.
- BugCrowd
BugCrowd is arguably the most creative platform of all, as it promotes traditional collective security testing services apart from bug bounty, attack surface management and a broad spectrum of penetration testing services for IoT and APIs. In addition, it has software development lifecycle integration capabilities, making the DevSecOps workflow easier and faster.
BugCrowds works with giants such as Amazon, Visa and eBay. In addition, its Bug Bounty section provides a SaaS solution that easily integrates into the software lifecycle, making it simple to run a bug bounty programme.
- SynAck
SynAck offers a highly skilled team with industry experience. The company combines artificial intelligence and machine learning-enabled security software with a collective collaborative network of hackers.
This platform takes an adversarial approach to exploit intelligence, to show the enterprise where the most business-critical vulnerabilities are and how they can be used against it. This intelligence enables resources across the systems development lifecycle to apply security best practices specific to their organisation.
- YesWeHack
YesWeHack is one of the European vulnerability disclosure companies, which generally attracts companies based in Europe itself, whose main concern is privacy and data protection. Recently, it announced 250% growth over 2020 in Asia, demonstrating its reliability, rapid rise and scaling to other geographies.
For this year, the platform has launched a training programme through DOJO to help hackers hone their skills. In this way, hackers around the world will be able to improve their software security testing skills.
- OpenBugBounty
OpenBugBounty has more than 1,200 active Bug Bounty programs. The key to the platform’s success is that it is the only non-profit platform, and allows coordinated disclosure of security issues on any website if the problem is detected by non-intrusive means.
The platform ensures that its security and disclosure policies are based on ISO 29147, for companies such as A1 Telekom.
Myths of Bug Bounty platforms
There has long been a belief that Bug Bounty should be publicly accessible to all hackers, until large companies such as Microsoft launched a bug bounty programme.
Open programmes are a method of publicly demonstrating the security of products offered by different companies, but in contrast, in a private programme a group of people are chosen to find bugs. So the vulnerabilities do not have to be public and the selected group of people have the expertise required by the company that hires their services.
Most organisations start with private programmes until the vulnerability management is tested, a reward budget is forecast and the legal teams are informed. This information is then made public, as publicly displaying security gives a sense of trust and honesty on the part of the company.
On the other hand, it is not necessary to run continuous bug bounty programmes, although many companies do; programmes involving short-range testing, using a defined number of compromised hackers in the short term, are sufficient.
The programmes are fully customisable, i.e. it is easy to set metrics for private programmes so that the number of reports received are manageable, both in time and budget. Once security teams are aligned, progress can be made towards a plan for ongoing engagement.
Alternatives to Bug Bounty platforms
In order for organisations to have a secure channel, it is necessary to have a vulnerability disclosure programme. Companies may choose to contract a penetration testing company to perform time-limited testing. This will ensure that the company has a trained and competent team.
Penetration testing usually lasts for a few weeks, whereas bug bounty programmes usually run for years, with no limit to the number of tests that can be performed.
The main difference between these types of programmes lies in the price, as companies pay penetration hackers by the objective to be achieved, whereas bug bounties are paid per valid vulnerability found.
Disadvantages
One of the main drawbacks, from a hacker’s point of view, is that you only get a reward when you are the first to find a bug or vulnerability. This results in economic instability within the Bug Bounty world.
From the companies’ side, it should be understood that it only makes sense to use these programmes if the company is powerful and stable enough to quickly fix the problems found. Also, if an organisation chooses to make use of public Bug Bounty, it must be able to deal with a considerable increase in alerts, many of which will be useless.
Finally, the vast majority of hackers working for these platforms are dedicated to searching for website vulnerabilities; very few choose to search for operating system bugs, as hacking network hardware or memory requires highly skilled expertise. Thus, if the company’s goal is to find bugs in its operating system, the reward will be more costly.
Conclusions
Bug bounty programmes are a great strategy to include in web testing and coding processes, as they provide a vulnerability perspective that in-house programmes cannot normally achieve.
These types of programmes are optimal for use on highly visible websites. Thanks to Bug Bounty platforms, the expertise of tens or hundreds of security researchers is available. Invitational bounties are approximately twice as successful as public bounties, mainly due to the quality of the bugs that hackers find because they are more experienced.
In general, a considerable increase of these platforms is expected in the coming years, and is an issue to be considered by any company, as it will be able to quickly fix vulnerabilities found in combination with other cybersecurity techniques.


