High volume of cyberattacks on industrial companies

The different cybersecurity challenges in industrial organizations’ control networks are the result of a rapid increase in functional requirements and the increasing use of information technology in industrial and industrial environments Manufacturing. According to an analysis by Kaspersky together with Business Advantage, many industry organizations believe they are prepared to deal with any cybersecurity incident, however, this trust may not be well-founded.
Kapersky’s study found that cyberattacks were mainly aimed at industrial enterprises (metallurgical, electrical, construction, engineering and others). They estimated that the number of industrial companies attacked in more than 50 countries amounted to more than 500.
The study, based on a survey of 359 cybersecurity professionals, showed that half of industrial companies experienced one to five incidents in 2016, and that on average, ineffective cybersecurity costs industrial organizations up to $497,000 per year.
The industrial landscape
Corporate and industrial networks, which form a multi-level hierarchical infrastructure in modern industrial enterprises, are increasingly integrated. New technologies are being used to improve transparency and process efficiency at the enterprise level, as well as the flexibility and fault tolerance of functions performed at medium and lower industrial automation levels.
This requires greater freedom of communication and integration of systems at all levels. At the same time, the functions related to the management of new systems, are becoming the responsibility of the IT department of the company.
According to Kapersky’s study, the result of all this is that the industrial network is increasingly similar to the corporate network, both in terms of usage scenarios and in terms of technologies used, and therefore the picture with respect to cyber threats d and modern industrial information systems are beginning to resemble the threat landscape of corporate computer systems.
With each passing year, the number of vulnerabilities identified grows compared to the number of problems eliminated. For example, according to US ICS-CERT, in 2016 that organization recorded 187 vulnerability notifications. During the same period, 139 closed and deleted vulnerability reports were published.
“The growing interconnection of IT (information technology) and TO (operational technologies) systems poses new security challenges and requires good preparation from board members, engineers, and IT security teams. They need a solid understanding of the threat landscape, well-calculated means of protection, and ensuring employee readiness,” said Andrey Suvorov, director of critical infrastructure protection at Kaspersky Lab.
On the other hand, according to Kapersky’s study, the three main countries that suffered industrial computer attacks in the second half of 2016 were Vietnam (more than 66%), Algeria (more than 65%) and Morocco (60%).
Vulnerabilities detected
Kaspersky Lab evaluated the current status of IT security components in industrial control systems (ICS) from different vendors. As a result of this investigation, 75 vulnerabilities were identified in ICS components.
The most identified vulnerability is DOS (denial of service) with 45 detected attacks, this vulnerability allows a denial of service attack to be performed remotely, and in the event of a successful attack the target software or hardware becomes unresponsive.
The next most identified vulnerability was RCE (remote code execution), with 16 attacks, which allows you to remotely execute arbitrary code on a target system.
With regard to the severity of these vulnerabilities at about 58 times the severity was very high, at about 15 times it was moderately high, and at 2 of the time it was less high.
Sources of infection
Kaspersky’s research showed that the percentage of industrial equipment under attack grew from more than 17% in July 2016 to more than 24% in December 2016. And the three main sources of infection were the Internet, removable storage devices and email attachments.
According to data from the Kaspersky study, in the second half of 2016 malware downloads and access to phishing websites were blocked on more than 22% of the industrial computers. “This means that almost every fifth machine faces the risk of infection or credential compromise over the Internet at least once,” Kaspersky said in a statement.
Removable devices (such as pen drives, external memories, etc.) are the second source of infection in an industrial network. In the second half of 2016, malware was% detected on 10.9% of the industrial computers when removable devices were connected.
It is important to note that in the ranking of malware attacks detected on industrial computers a high percentage were associated with malware of the following classes: Virus, Worm and Net-Worm. And the malware in these classes uses removable devices and network folders as their main distribution channels.
Since malware frequently hides its presence on the system by infecting existing files or using similar names, it can take the user a long time to realize that the files are infected.
Malicious e-mail attachments and malicious scripts embedded in the messages were blocked on the 8.1% of the industrial computers. In most cases, attackers use ordinary phishing (email messages that, as a rule, mimic messages from banks, delivery services, etc.) to capture the user’s attention and hide bad intentions.
Usually, malware is distributed in malicious emails in office document formats, such as MS Office and PDF, manipulated with malicious scripts and vulnerabilities in relevant applications.
Types of malware used in attacks
According to Kapersky’s study, in the second half of 2016, a total of 20,000 different malware samples were detected in industrial automation systems that belonged to more than 2,000 different malware families.
In most cases, attempts to infection industrial computers are sporadic and malicious functionality is not specific to attacks on industrial automation systems. This means that all threats and categories of malware affecting non-industrial companies around the world are also relevant to industrial companies.
These threats include Trojan spies, financial malware, ransomware (including ransomware encryption), backdoors and Wiper-like programs (KillDisks) that leave your computer unusable and clean up your hard drive data.
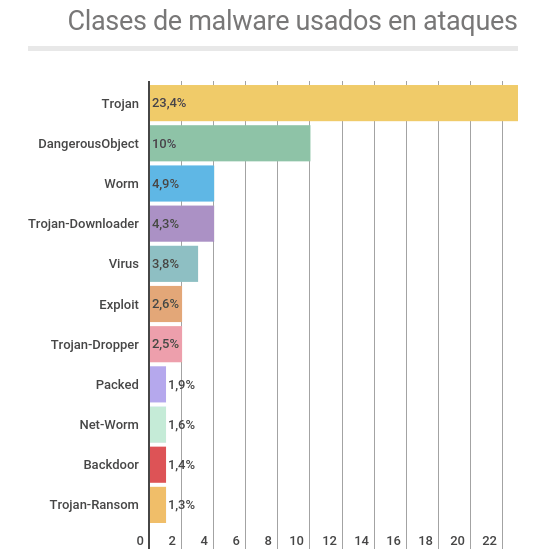
In addition, according to data from the study, botnet agents (malware that can be controlled remotely via command and% control servers) and/or traces of their activity on the 5 of all the industrial equipment attacked were detected.


