Cybersecurity is indispensable in remote work

Telework is a concept that has been around for years, yet the recent Covid-19 pandemic has increased the number of teleworkers to unprecedented levels worldwide. Many governments and companies are adopting social distancing techniques to limit or slow the spread of the virus, from closing down all educational institutions to asking all companies to try to make it easier for their employees to work from home.
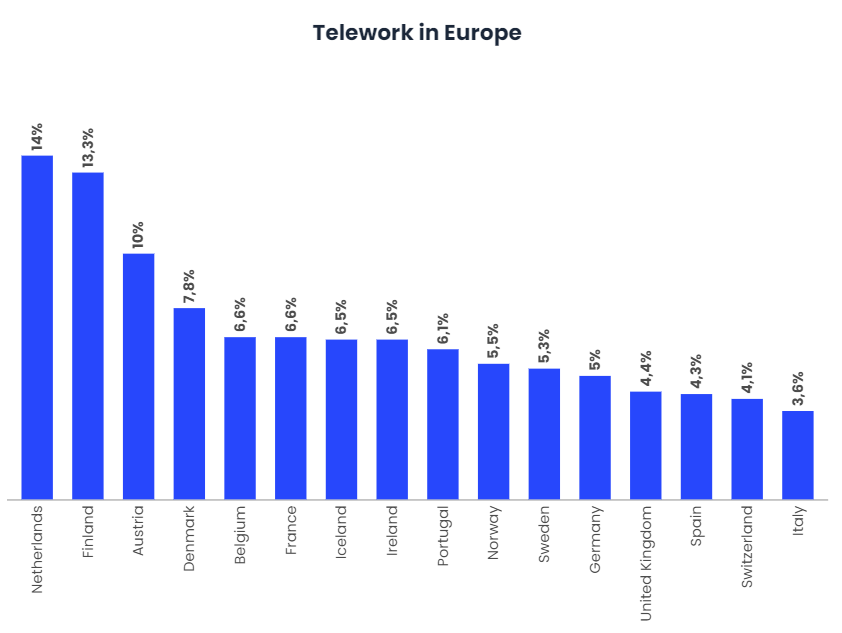
In addition to ensuring that networks, VPNs, and other IT resources are capable of supporting such change, organizations that have not incorporated such teleworking into their disaster preparedness plans should be aware of and take steps to mitigate cyber security and data privacy.
In Spain the option of working remotely is among the first measures taken by companies (18%) behind the disinfection of workplaces, the closure of some sectors, and the sharing of information among staff.
The most common threats
Although many companies already have remote working policies and are well equipped for this type of work environment, they are not exempt from managing the cyber security risks that can arise as the number of employees working from the comfort of their homes increases dramatically.
Security measures in a teleworking environment should cover information systems and technology, and all other aspects of the information systems used by the employee, including paper files and other media, such as storage devices and telecommunications equipment.
It is important to remember that just because employees work from home or another approved alternative location, it is still their responsibility to protect and manage records and other confidential information stored on teleworking devices and transmitted over external networks. Employees working from home need to keep property and information secure and separate from their property and personal information.
Parallel to information privacy, workers who perform their tasks remotely and their organizations must be aware of a number of threats:
- Unsecured personal networks and devices
Having to move quickly from the office to their home, many employees may have to use their personal devices and home WiFi networks to work. Both often lack the protection systems built into business networks, such as firewalls and anti-virus software.
- Phishing campaigns and fraudulent calls
Working from home means that many employees will rely on email and telephone as their primary methods of communicating with their organizations. This increases the risk of impersonation to obtain information such as login details that can lead to a security breach.
- Ransomware and spyware
Operating on a network or personal device, along with the possibility of receiving an impersonation email, increases the chances of ransomware or spyware being loaded onto an organization’s computer systems.
How do we deal with these threats?
Making some simple decisions to maintain “good cyber hygiene” can help limit the chances of a security breach.
For security professionals, this means knowing who is connected to your network, monitoring unusual or unexplained behavior, and having a plan to stop or remedy any violations that may occur, including clear and relevant communications for everyone in the organization.
Some simple steps that can help a worker maintain a good level of cyber security while working from home are:
- Installing the latest software updates on the device
Keeping up to date with patches and software updates for each device is a simple, but effective way to ensure you have the latest defenses to address security vulnerabilities.
To avoid downtime, it’s a good idea for workers to set up updates to run automatically overnight.
- Installing an Antivirus
Many operating systems come pre-installed with an anti-virus. However, if the device does not have the software installed, there are several free solutions available, although they are not always the most suitable option.
- Secure password and two-factor authentication
It is important to use different passwords for each of the accounts. While it may be tempting to allow the web browser to store the passwords, it is advisable to use a password manager instead, to create, remember and auto-complete all the necessary passwords.
Or, the company can go one step further and set up a two-factor authentication. This will protect the employee’s account in case the password is leaked in a data breach. With this method, each employee will be required to complete an additional step when logging into their account, which can be a text message, an email or a biometric method.
- Public WiFi and VPNs
While teleworking allows each employee to perform their tasks from a different location such as a cafe, hackers can take advantage of this opportunity and attack the device if they both use a shared network over public WiFi.
In this situation, it is recommended that each worker choose to use a personal access point instead, and use your organization’s VPN that will encrypt the web connection, making it unreadable to anyone trying to intercept it.
- Watch out for phishing
As discussed above, phishing is one of the most common cyber threats, often taking the form of an email requesting personal information, embedding fake links, or attaching a virus.
Workers should be on the lookout for such emails as the sender may appear to be someone they know and should never share their personal information in an open email or attachment if they are not expecting it.
- Work devices are non-transferable
As selfish as it may seem, it is important not to allow family members to use work devices. Family and friends are not aware of the company’s IT security protocols and may unintentionally violate them or even download malware that can quickly spread through the organization’s systems.
- Confidential data
If the worker needs to access confidential data while working from home, the company must ensure that all information is maintained within its organization’s systems and network. To do this, the employee must work directly on the server that hosts the data, taking advantage of the fact that companies have many firewalls and better protection built into their systems than individual computers may not have.
- Block devices
Devices should never be left unattended, and hard drives should always be encrypted. Because, in the event of a theft or loss if the hard drive is encrypted, at least the company has the peace of mind that its data is safe.
Official guides
In response to the drastic increase in employees working remotely, some organizations in different countries have provided official guidelines, which advise how to act so that this form of employment does not trigger a business crisis.
In the United States, the U.S. Federal Trade Commission (FTC) and the US National Institute of Standards and Technology (NIST) have issued guidelines for employers and employees on best practices for safe teleworking. In addition, the Cybersecurity and Infrastructure Security Agency (CISA) has provided advice on identifying critical workers, including IT and cybersecurity personnel, in critical infrastructure sectors who should maintain normal working hours if possible.
At the national level, no guidance has been published, however, the institutions recommend maintaining a healthy work routine, providing workers with all the necessary tools to be able to perform their tasks without much disruption.
Working from home, the organization of tasks and priorities may seem a little more confusing than in the office. To optimize this point there are programs that help consult pending tasks, prioritize, delegate tasks to other team members, etc.
However, having too many applications to organize is as bad as having none at all. It is recommended that each company choose the only ones necessary, that are more intuitive for your workers and that adapt better to the type of work they do. The best tools are those that allow you to connect on different platforms, always offering the same results.
The last advice from the authorities comes in relation to the control of the working day. A worker who performs his work duties remotely is committed to performing his working day 100%, working neither more nor less hours than those contracted and carrying out a schedule control.
Conclusions
One of the key preventive measures for the spread of Covid-19 is social distancing. Fortunately, in this increasingly connected world, one can virtually continue one’s professional and private life. However, with large increases in the number of people working remotely, it is vital that special attention is also paid to “cyber hygiene”.
While it is always preferable to establish clear policies for remote working and training in advance, in times of crisis or other rapidly changing circumstances, this level of preparedness may not be feasible. Fortunately, there are specific research-based steps that executives can take without much effort to improve the commitment and productivity of their employees, even when there is little time to prepare.


