According to the latest reports, the cryptocurrency industry is plagued by theft and fraud despite increasing regulatory attention to security and money laundering issues.
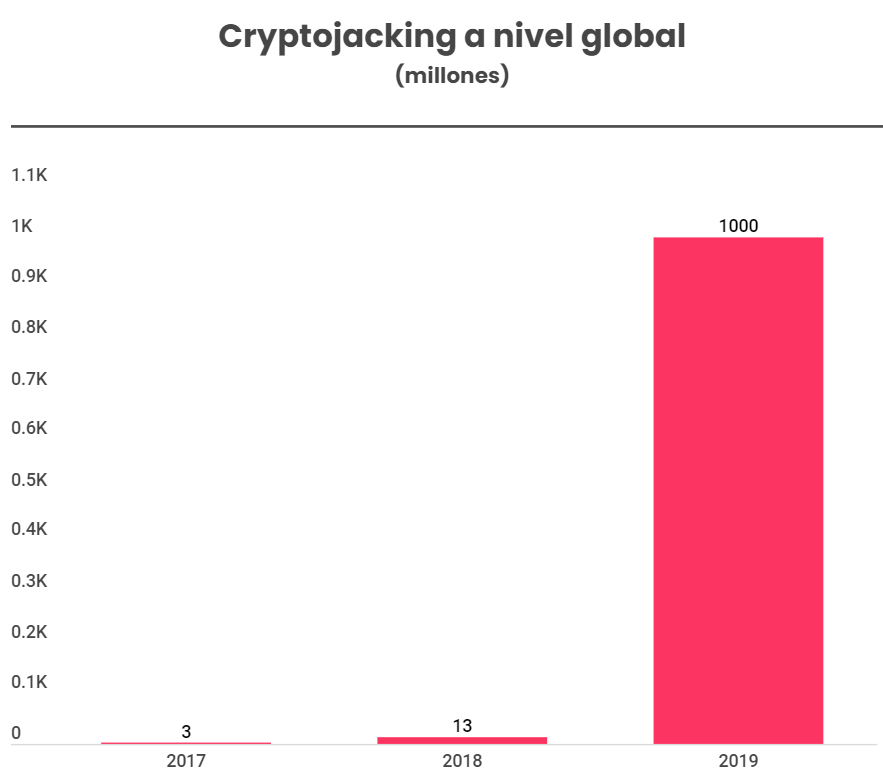
In the first quarter of 2019, cyber criminals managed to extract more than $356 million, including the QuadrigaCX scam that cost cryptocurrency owners nearly $195 million. If the trend persists, the losses incurred by the industry due to cyberthefts and scams will exceed $1 billion by the end of the year.
In the UNITED alone, 30% of the companies in 2018 were the subject of cryptojacking, and only 67% of them had preventive measures in the face of these possible thefts.
Like denial-of-service attacks, cryptojacking is simply another way in which attackers can take advantage of profits earned using someone else’s computer and network resources. However, it affects not only traditional desktops and laptops, but also mobile devices.
Mobile Cryptojacking
Mobile cryptojacking usually occurs when end users download fake apps or by malicious scripts that hackers inject into vulnerable web pages. This can slow down your smartphone while also affecting your network bandwidth.
According to the latest findings, malicious codes affecting mobile devices represent the extraction of nearly 5 of the entire volume of the Monero cryptocurrency, which equates to more than $100 million.
While evidence shows that mobile cryptojacking is growing, mobile platforms like iOS and Android offer more security than traditional workstations. In 2018, Apple announced new encryption restrictions on iPhones and iPads, mitigating the threat on iOS. While this can help minimize the associated risks, it certainly doesn’t eliminate them.
Recently a new form of cryptocurrency theft malware has been identified in the Google Play store, dubbed “clipper”. It was discovered within an application that impersonated MetaMask, a complete browser extension that allows Ethereum-based applications to run in a browser without running a full Ethereum node.
Another user-centric practice that can be implemented to combat this threat focuses on the development of anti-phishing programs, aimed at mobile devices, and, of course, ongoing training and awareness-raising initiatives Security.
In particular, phishing has become an industrialized process. It is estimated that approximately one in 2,000 emails is a phishing email and more than one million fake websites are created each month to try to trick users into disclosing personal information. A recent study showed that 25% of phishing emails bypass the security of Microsoft Office 365.

After all, most mobile devices have a lot of apps installed, and with over 3.8 million apps available to Android users on Google Play, more than 2 million apps on the Apple App Store and over 1.5 million apps in other third-party stores. There are many opportunities for hackers to introduce malicious content.
However, all of the above efforts can only be enough to prevent malware attacks for mobile devices, as there is no perfect security program or a user who makes good decisions constantly.
Browser-based Cryptojacking
Unlike the profitability of mobile cryptojacking, attacks aimed at profit through the browser have lost strength in recent times. This decline could be due to a number of reasons.
One possibility is that the recent drop in cryptocurrency prices has made in-browser mining less profitable. Since the browser is nothing more than an application on a device, it cannot generate the same computing power as the infection on a real device. As a result, this type of cryptojacking takes much longer to generate each currency, which may incentivize criminals to refocus on faster malware infections.
In addition, the fickle value of cryptocurrencies could encourage cybercriminals to choose a completely different source of income, which makes cryptographic malware have a higher share of activity, although nominal levels may have Decreased.
However, this browser-based drop in cryptojacking is strongly linked to the closure of Coinhive, the world’s leading mining malware sales company.
With Coinhive missing, criminals would have to turn to other providers in order to get what they need and carry out their crimes. And although, there are many other providers of the same type of scripts, removing this company could affect the overall ability of less technically expert attackers to create web-based cryptojacking attacks.
However, some experts predict that, browser-based cryptojacking may experience a resurgence in the near future due to the recent sharp drop in Monero hash rate. A reduced hash rate makes each coin’s extraction less computing intensive, making cryptojacking a more cost-effective option despite its lower collection power.
Despite these ups and downs, browsers keep working to keep their defenses high against this dipo of attacks. For example, the development team behind Mozilla Firefox announced an initiative to block encryption scripts.
This move prevents cybercriminals from being able to steal through the browser. Engineers have even responded to one of the relevant bug reports by uploading a tutorial on how to disable adverse activity. The corresponding feature will complement Mozilla’s Content Blocking privacy toolkit in the near future, which will take effect in Firefox v67.
The new browser anti-tracking technology is based on Disconnect, which has provided a list of domains that serve these abusive scripts. Disconnect also currently offers a Chrome extension that offers similar anti-tracking services in Google’s browser.
Cryptojacking in the cloud
Finally, the latest reports indicate that nearly half of organizations have malware in one of their cloud applications.
In particular, this year, cryptojacking malware in the cloud has become one of the biggest threats to organizations. This malware offers cyber-criminals the ability to regularly steal the processing power of devices and other resources to exploit the cryptocurrency.
As such, it should come as no surprise that hackers are targeting vulnerable data centers and websites that can help them improve their mining capabilities.
Public cloud platforms, particularly IaaS platforms, are particularly popular targets for cryptojackers, as they offer a lot of processing power in an environment where attackers can go unnoticed.
A recent example of high-profile cryptojacking and cloudjacking in action was the discovery that some of Tesla’s Amazon Web Services (AWS) instances were appropriate for unwanted use: mining.

In Tesla’s example, attackers ran various mining programs and concedediped IP addresses, effectively disguising their activities from conventional firewalls and intrusion detection systems. They also deliberately accelerated mining software to run at a speed that would not activate high-use detectors.
Conclusions
The fluctuations within the cryptojacking have remained since its inception, and everything points to them remaining the same in the near future.
On mobile devices cryptojacking is no different from any other threat. Security and IT personnel must be on board, users need to know what to do and what not to do, and executives need to understand what’s at stake. No one really has all the right controls, visibility and knowledge, especially when it comes to mobile devices.
On the other hand, the first steps by browser providers to defend against these attacks are definitely welcome, however, they are not likely to influence the large-scale epidemic. Instead, the closure of Coinhive is a much more promising initiative to counter this trend.























