Confidential Computing: data security in data processing

In recent years, there has been concern about protecting data or workloads during their storage in the cloud or movement across the network, but what about during their processing? Data must be protected while it is running, and this has been a challenge. Encryption as we have known it is inadequate in this area, as applications need access to data in an unencrypted form while it is running.
The need to minimise data exposure in the cloud led to the creation of Confidential Computing, a security model that provides a trusted, hardware-based data execution environment. Confidential Computing aims to limit access and ensure data protection while workloads are being processed by using a Trusted Execution Environment (TEE) to protect data in the cloud.
In August 2019, the Confidential Computing Consortium (CCC) was established under the mandate of the Linux Foundation working hand-in-hand with hardware and software vendors such as Intel, Google, Microsoft, IBM and Red Hat. The ultimate goal of the CCC is to create a system that is secure without relying on proprietary software for confidential computing environments.
What is Confidential Computing?
Data is isolated using hardware-based techniques, performing in-memory data encryption without showing the data in the cloud to the whole system. As discussed above, the data is stored in TEE, where it is impossible to see the data from the outside, even with a debugger. A TEE provides a protected container (like a black box on aeroplanes), because it protects part of the processor and memory. You can run software on the TEE to hide parts of the code and data so that they cannot be seen or modified from outside the trusted execution environment. These encryption mechanisms eliminate unauthorised external access. Confidential Computing therefore isolates the software and data from the underlying hardware, the latter being encrypted.
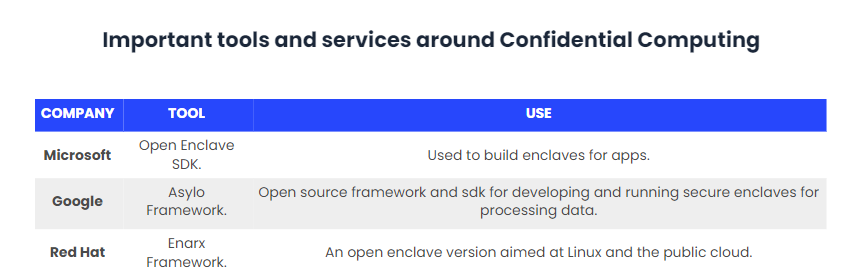
An example of this is the use of tools such as Intel’s Software Protection Extensions (SGX), which can be used to encrypt data in memory or use an SDK to create TEE in firmware. Microsoft’s SDK offers an open source framework that allows developers to create TEE applications using a single abstraction, and Red Hat’s Enarx and Asylo Project offer similar abstraction layering. In any case, Confidential Computing requires collaboration from a wide variety of industry companies, including hardware vendors, cloud providers, developers, open source experts, academics and more.
Why Confidential Computing?
Security is the key to accelerating the adoption of cloud computing. Confidential Computing is the tool to migrate highly sensitive IP addresses and data to the cloud. The key benefits of Confidential Computing are:
- E2E security encryption.
- Data protection in execution.
- Greater customer control in the cloud.
- Increases transparency and builds user trust.
- Ensures protection against unauthenticated use.
- Facilitates movement between different environments.
Players on the market
The different companies that are part of the CCC offer their own products with their own particularities and, sometimes, focused on different sectors. Microsoft Azure, Google Cloud or AWS Nitro, among many others, are worth mentioning.
Most importantly, Microsoft Azure helps minimise the attack surface for stronger data protection. Azure already offers many tools to protect data at rest and to encrypt data in transit via secure protocols such as TLS and HTTPS. Now it introduces in-use data encryption.
Among its services it offers preventing unauthorised access, intellectual protection of the organisation in the cloud by maintaining full control of data to comply with government regulations, addressing issues by combining data across organisations to unlock data analytics, and products that remove liability for private data with blind processing so that the service provider cannot even retrieve user data.
In turn, Google Cloud offers real-time encryption of data in use by leveraging the security technology offered by modern CPU. It also ensures lift-and-shift confidentiality, the ability to use confidential virtual machines without the need to modify application code. Organisations can collaborate on research projects in the cloud from any geographic location without compromising confidentiality.
IBM, for its part, has been investing in end-to-end Confidential Computing for its clients’ cloud computing for more than two years with products such as IBM Hyper Protect Cloud Services and IBM Cloud Data Shield. In his view, data protection is only as strong as the weakest link in end-to-end defence, which means data protection must be global. During 2020, he announced IBM Cloud for Financial Services and IBM Secure Execution for Linux, along with new homomorphic encryption toolkits.
The latest company to venture into Confidential Computing has been Amazon with AWS Nitro Enclaves, which is a combination of software and hardware enhancements to the Amazon EC2 platform. Amazon has moved network virtualisation and storage virtualisation to a dedicated hardware appliance that frees up the CPU to run additional virtual machines. An application running on the same EC2 instance can access Nitro Enclave. AWS Nitro Enclaves do not have an IP address, persistent storage, or user access. As such, they cannot be associated with a VPC and do not expose any APIs or endpoints to the outside world.
The future of Confidential Computing
The development of a common cross-industry framework such as the CCC is exciting as there is immense collaboration to drive the technology forward, and at the same time, it is a competition between the companies that make up the CCC. It is therefore the best example of the success of Confidential Computing, which allows highly sensitive information to be shared and exchanged with other parties without actually exposing it – only a set of data is shared. Thus, it is possible to collaborate and perform joint functions on highly sensitive information quickly and easily by simply not allowing that information to be exposed to unwanted parties.
Recently, Google Cloud published on its blog the opinion of some of its partners on the service provided by Confidential Computing. Among them, Mark Shuttleworth, CEO of Canonical, reported that the collaboration between Google and Canonical ensures that Ubuntu is optimised for GCP operations. Canonical Ubuntu is fully compatible with confidential computing in the Google Cloud, providing a new level of confidence in the public cloud infrastructure.
Another great collaboration has been between Thales and Google Cloud. The two have collaborated in a number of areas, but Kubernetes Secrets, which holds sensitive data such as passwords, keys and certificates, stands out. Also HashiCorp Vault, which allows teams to securely and tightly store access to tokens, passwords, certificates and encryption keys to protect machines and applications.
Conclusions
The use of Confidential Computing enables customers to run highly sensitive workloads in the cloud, minimising the risk of insider access. Along with data-in-transit and data-at-rest encryption, data-in-use encryption is the third pillar of E2E encryption. This tool, Confidential Computing, is based on the use of hardware-based Trusted Execution Environments (TEE).
The creation of the Confidential Computing Consortium supports this new approach to security, and aims to define standards for the use of Confidential Computing by supporting the development and adoption of open source tools. The CCC is committed to creating a system that is secure without relying on proprietary software for confidential computing environments.
Currently, there is a wide range of offerings in the Confidential Computing market, such as Amazon which relies heavily on the Amazon EC2 design, or Microsoft and Google whose offerings are based on the security enhancements of Intel and AMD processors. All these large companies are betting heavily on the use of Confidential Computing.


