The Premera Blue Cross Hack – An Analysis
Premera Blue Cross, which provides health insurance services primarily in the US Northwest to approximately 1.6 million customers, announced March 17 a major network intrusion that has compromised financial and medical records for about 11 million people. This is the second largest breach on the Department of Health and Human Services' tally of major breaches.
The attack pattern is very similar to the Anthem attack of early February, and seems to be part of a very carefully planned Advanced Persistent Threat (APT). As in the Anthem case, early information suggests this could be a state-sponsored attack, though there are still no official declarations from the authorities and the group performing the research.
According to Premera, the initial attack occurred May 5, 2014; but it went unnoticed until January 25, 2015. In other words the introducers had 8 months to gain broader access to Premera’s infrastructure and exfiltrate confidential information.
An APT is usually defined as a set of sophisticated computer hacking processes that are performed stealthily and continuously by humans targeting a specific company. It requires a high degree of covertness during a long period of time, while data is slowly extracted.
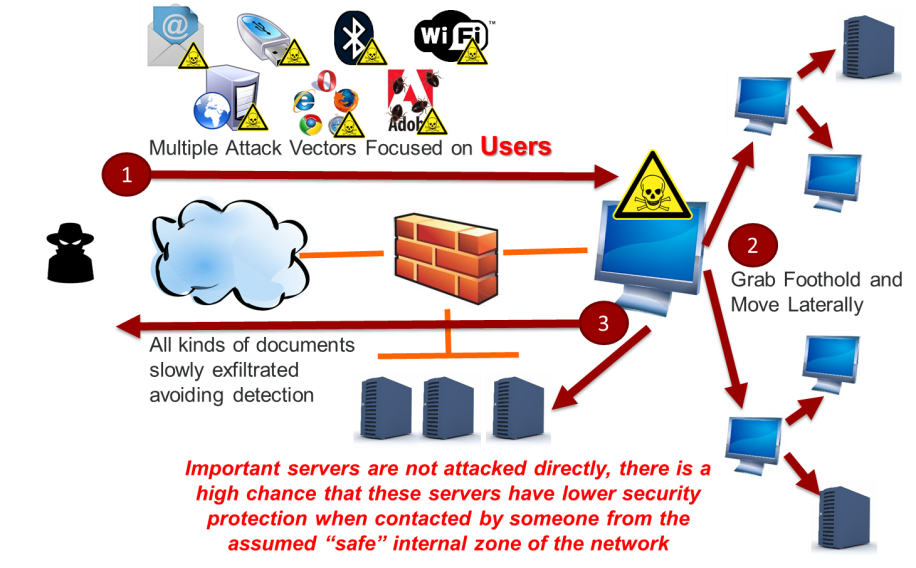
 A typical APT data breach starts with an attack on a “human” component of the targeted company to avoid the perimeter protection, which is typically where companies invest most of their security resources and budget. The attack could have materialized in the form of a CD or any other storage form, email, software or mobile device carrying malware that an internal actor connects to the network, thus infecting it.
A typical APT data breach starts with an attack on a “human” component of the targeted company to avoid the perimeter protection, which is typically where companies invest most of their security resources and budget. The attack could have materialized in the form of a CD or any other storage form, email, software or mobile device carrying malware that an internal actor connects to the network, thus infecting it.
The malware starts “crawling” laterally to find what it’s looking for. Once found, it sends information to the attacker in a way that is really difficult to detect if you don’t know what you’re looking for. That’s why these breaches take so long to be detecte.
What can be done to mitigate these risks?
Personnel training is very important. Proper training acts as a perimeter protection at the person level. Everyone with access to confidential information, whether they are employees, covered entities or business associates can be tricked, and we must ensure that information will be safe from these types of attacks.
There are also technical measures that can be implemented. We recommend Data Encryption so that direct unauthorized access to the databases will find information that is unusable without decryption keys. Encryption can be implemented not only at a disk level, as stiupulated by HIPAA, but at a record level within the database. This would add mitigation for a specific risk zone, but would require more effort on the adjustment of applications to use this type of encryption with databases.
Another mitigation action could be segmenting the internal network creating subzones, interconnected with firewalls to segregate the information, i.e. acting as independent networks while removing the trust among them. Then implement good access control mechanisms to restrict the access of authorized personnel to only those pieces of information they need access to in order to perform their work.
Data Loss Prevention can add an extra layer of protection. This consists of: 1) a specialized tool to review all the information that is leaving a company’s computer, whether internally or externally, properly configured to raise alerts depending on business rules previously defined. 2) A team of specialized security professionals devoted to maintain the tool, configure such rules, review the logs, and report on the obtained information. The important part is to understand what “normal operations” look like in order to identify patterns that appear questionable. The output of this security piece can be paired with a Security Operations Center that would be devoted to catch relevant network alerts, business applications and security tools to identify potential security breaches and kick off timely and proper investigation.
The Anthem case raised many flags about large attacks on the healthcare industry, especially this type of Advanced Persistent Threats. Premera should reinforce all those voices and help companies become aware of their actual risk to strengthen their security measures. We don’t know if there are more companies already under attack right now – we will see over the following months.


