What is Cyber Threat Intelligence used for and how is it used?

The great technological evolution experienced in recent decades is bringing great benefits to society, generating resources that facilitate daily life and making human beings more efficient. Provided that the technology is used in the right way.
However, cyber criminals also take advantage of the advancement of technology, i.e. many criminal operations are carried out through the use of cyber resources. This allows cybercriminals to hide their identity and, moreover, they can commit such operations from any location.
As such, threats continue to advance at a rapid pace, as does technology, which means that a company’s defences will be compromised if they continue to use traditional security measures or if operational approaches are not adequate to today’s threats.
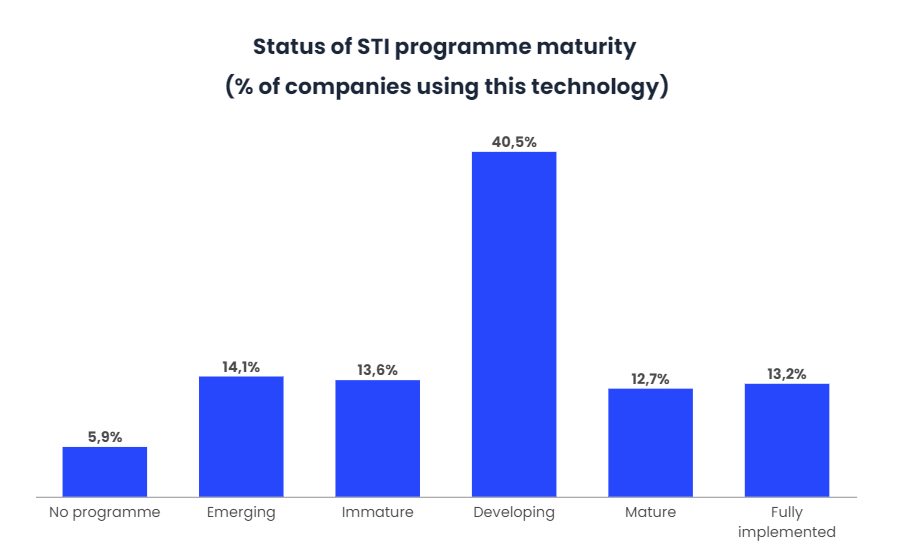
In Europe, the concept of Cyber Threat Intelligence (CTI) has emerged to combat the wide variety of threats that are emerging. Currently, only 5.9% of companies have no CTI programmes in place, while 40.5% of companies report that their CTI programme is under development.
What is cyber security threat intelligence?
To define this concept correctly, CTI is what cyber threat information becomes once it has been collected, assessed and analysed through rigorous and structured techniques. This type of intelligence provides added value to the information, reducing uncertainty for the consumer and the time it takes for the consumer to identify threats and opportunities. CTI requires analysts to identify similarities and differences between information, being able to detect deception to produce concise, high-value intelligence.
The process of developing this intelligence technique is not E2E, but is a circular process, known as the intelligence cycle. The analysis part of the cycle is what differentiates intelligence from information gathering and dissemination. Analysis always depends on the capability of the experts, taking into account their techniques, tactics and procedures (TTP). In this way, forward-looking strategic and operational assessments can be made.
CTI seeks to generate knowledge around the adversary in order to reduce the potential risk that can impact on any business and organisation, it does not represent something as basic as just looking for indicators of compromise on threats. It will always seek to pre-empt and counter attacks by analysing a threat as a whole to detect key data that helps identify the cyber criminal behind an attack.
It is therefore essential to apply hypothesis- and evidence-based analysis techniques through an analytical process of all collected data. The key questions of these hypotheses that must be asked in this model are: who are the attackers, what do adversaries use, where do they usually attack, when do they act, why do they attack and how do cyber criminals operate.
Thus, a Cyber Threat Intelligence product consists of two elements: context and action in order to be understandable and actionable by the consumer.
Types of threat intelligence
Currently, there are four types of CTI: strategic, tactical, technical and operational. All four are fundamental to building a comprehensive threat assessment.
- Strategic intelligence
This refers to potential cyber-attacks and the possible consequences for the non-technical consumer and its parties, as well as for decision-makers. Strategic threat intelligence is delivered in the form of technical documents and reports, and takes the form of a detailed analysis of emerging risks and trends in the world. Basically, it involves a high-level overview of the threat situation of a type of industry and organisation.
- Tactical intelligence
Tactical intelligence is responsible for providing information on the tactics, techniques and procedures (TTPs) employed by cyber criminals. This type of intelligence is aimed at the people in the department involved in the protection of IT resources and data, providing details on how a company can be attacked based on the latest developments in the type of attacks and the best way to defend against and counter the attacks.
- Technical Intelligence
The information provided by technical threat intelligence is based on signals that indicate that an attack is being initiated, such as phishing or social engineering. Often this type of intelligence is associated with operational threat intelligence, although it adjusts as cybercriminals act on tactics to take advantage of new events. This intelligence plays an important role in blocking social engineering attacks.
- Operational intelligence
In this case, information is gathered from a variety of sources, such as social networks, antivirus logs, chats and past events. Through this intelligence, the nature and timing of future attacks is anticipated. For example, machine learning and data mining are used to automate the processing of a multitude of data points in different languages. In this case, it is the security and attack response teams that use this type of operational intelligence, so they can change the configuration of controls such as event detection rules or firewall rules along with access controls.
What is the threat intelligence lifecycle?
As mentioned above, the threat intelligence development process is circular, and there are several key points involved in the threat collection process:
- Goals and objectives
This step selects the right threat intelligence sources and tools for an organisation to use to implement threat intelligence into its solutions and security strategy. This will help security teams to stop potential threats identified during the threat modelling exercise by obtaining data and intelligence tools that generate up-to-date information on threats considered to be of high risk and impact.
- Data collection
Data collection elements such as internal systems, cloud services and security controls are central to this cycle. However, it is necessary to collect data from different third party threat data sources to obtain information on the latest TTPs. Third-party sources can be social networks, antivirus logs and threat research reports, hacker forums and malicious IPs.
- Data processing
Data processing and data collection is necessary to create the CTI, so automated intelligence processing is a prerequisite. In case you want to filter the information manually, add metadata and correlate and aggregate the different types and sources of data. Therefore, CTI applications employ machine learning to automate the collection and processing of data to provide information on a continuous basis.
- Analysing data
Data analysis is the location of answers from processed data to questions such as when, why and how a suspicious event occurred. This provides insight into the origin of an incident and what information the cybercriminal was looking for, as well as the preferred methodology of attack.
Threat intelligence tools
Another factor to consider is that threat intelligence services provide organisations with information related to possible sources of attacks relevant to their business and consulting services. Some of the tools that make it easier for different organisations and companies to gather data and threat intelligence are:
- Anomali ThreatStream gathers threat intelligence from various sources and provides tools for investigations.
- Cyberint’s Argos is a SaaS platform designed to analyse an organisation’s attack surface and cyber attacks targeting its industry from open, deep and dark networks.
- Kaspersky Lab’s Kaspersky Threat Intelligence collects petabytes of data to generate threat intelligence feeds of actionable cyber threat data and information about threats targeting particular industries.
Conclusions
In conclusion, this type of threat intelligence strategy and teams are emerging and evolving to meet the needs of any organisation’s or company’s security operations centre.
Teams must also focus on a strategy that includes strategic threat intelligence, incremental programme growth to provide direct incident support, and tactical and operational threat intelligence to guide decision-making during incident investigation and threat detection.
CTI serves and is used to provide context and conclusions about active attacks and potential threats to facilitate decision making by the company’s security teams.


