What can we expect from Cybersecurity in 2021?

2020 has been a year that all people, everywhere in the world, will remember forever, and not just as a good year, but as a year in which all aspects of our lives have been affected by the worst public health crisis in decades. The COVID-19 pandemic has changed our daily lives, exposing collective fragility and increasing feelings of fear and uncertainty. The paradigm shift will undoubtedly have profound and lasting effects.
Some of these changes are related to the adoption of technology, as the global emergency has made people hyperconnected, making technology part of their daily lives much more than before. Many of these technological innovations were not expected to come for some time, in fact, as dependence on connectivity increases and the digital transformation accelerates, the crisis may have even anticipated what was previously thought to be coming in the near future. And just as the adoption of many technologies has accelerated, so too have the challenges of cybersecurity accelerated.
Cybercriminals have adapted very quickly to the new reality, taking advantage of the unique opportunities that came with the general anxiety and rush to adopt telework. Businesses and the workforce were unprepared to deal with the cyber risks that came with the change, almost overnight, brought about by the new normality.
How is the market?
Cybersecurity has become one of the biggest challenges for companies in recent years. In 2019, data leaks exposed 4.1 billion records, and in the same year, the global average cost of a data breach reached $3.92 million.
Given this data, it is not difficult to understand why global spending on cybersecurity is expected to reach $110.99 billion by 2025.
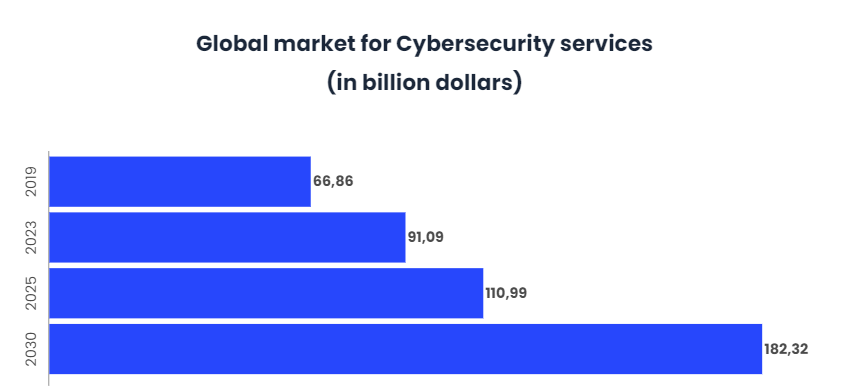
The COVID-19 pandemic has become a catalyst for exponentially increasing cyber security threats and making businesses susceptible. In fact, cyber attacks on FinTech have increased by 238% with the arrival of the pandemic, coronavirus related attacks have increased by 605% in the second quarter of the year, in addition, phishing and ransomware attacks have grown by 50% this year, and what is more shocking is that a single hacker has stolen 34 million user records from 17 companies this year.
However, all this has caused 80% of companies worldwide to increase their digital security infrastructures, change their strategies and educate their employees about security. All in an attempt to deal with this increase in cyber-threats.
What can be expected in 2021?
As businesses seek to make the transition to a new normal, the question is what will happen in 2021 in the cybersecurity landscape? What will be the main approaches, risks and considerations for leaders and practitioners in the coming year?
What is clear is that organizations must be better prepared for what lies ahead, to reduce security risks as they seek to prosper and remain competitive. To do this, they must start thinking outside the box by 2021, and consider the following cybersecurity trends and predictions.
Remote workers will remain an important focus
Telework is here to stay, many companies are laying the groundwork to establish it and continue with this methodology after the pandemic. This will cause cybercriminals to continue launching attacks that exploit the behaviour and habits of users and workers.
Throughout this year, cybercriminals have taken advantage of the changes and impact caused by COVID-19 to launch phishing, vishing, ransomware and a host of other attacks targeting security breaches in businesses, as many were not prepared to support a remote workforce in a secure manner. For example, prior to the pandemic, nearly 82 percent of businesses allowed their employees or partners to carry their own devices (BYOD). However, 72% had no protection whatsoever against BYOD malware. As the pandemic has led to an exponential increase in BYOD, this lack of preparedness is potentially worrying.
So far in 2020, not knowing how to support teleworking without exposing confidential information has led to nearly 25% of organisations paying unexpected costs to address security breaches. In fact, this movement towards telework has left organisations unprepared to monitor or identify internal threats due to unauthorised remote access, weak passwords, insecure networks and the use of BYOD. These patterns are expected not only to continue, but to skyrocket in 2021 and beyond.
If organisations do not reconsider their security approaches, cyber attacks will continue to evolve and exploit teleworkers as ideal entry points into corporate IT ecosystems.
Threats in the cloud
As teleworking and online collaboration intensify, the adoption of the cloud has become the perfect ally for companies to ensure business continuity. And although companies were already migrating to the cloud before the crisis, the pandemic has acted as a catalyst for the same. In fact, global market spending on cloud services is expected to reach $1 trillion by 2024, at a compound annual rate of 15.7% over the 2020-24 forecast period.
This adoption of cloud services will continue to increase in the long term. However, the rapid migration to the cloud is introducing a number of new security threats and challenges. Protecting these assets means that organisations will have to focus their efforts on improving their cloud security programmes.
By 2021, attacks on the cloud are expected to continue to be executed through:
- Stolen credentials, usually through phishing.
- Exploitation of misconfigurations in the cloud, including misconfigured cloud storage, reduced visibility, control, and incomplete deletion of data
- Hacking into vulnerable applications in the cloud.
Prevention and detection strategies will be crucial for all organisations, large or small, to protect themselves against these threats. Expanding the use of the cloud will require organisations to improve the visibility of their cloud presence, assets and vendor relationships to manage risk.
Goodbye VPN, hello Zero Trust
To rapidly increase remote operations and comply with stay at home regulations, many organisations looked to legacy security architectures such as VPNs as a miracle solution for teleworking.
However, this is not a good long-term solution as VPNs introduce latency, hinder productivity, can be difficult to scale and can give employees excessive access to internal resources. In addition, VPNs can be easily exploited by cybercriminals, even if the configuration and implementation of the VPN has been flawless.
With 400 million businesses and consumers using VPNs worldwide, it is likely that cyber criminals will continue to exploit VPNs for successful attacks.
Fortunately, more and more companies are becoming aware of the problems of VPN usage and are gradually eliminating them in favour of implementing Zero Trust security models. With this model, users only have access to the smallest set of permissions required to perform their work tasks, which they access through strong identity authentication services. That is, once the worker’s identity is authenticated and the integrity of the device he or she is accessing is proven, authorization and access to just enough resources to perform the task at hand is granted.
This trend towards access to the Zero Trust security network will accelerate in 2021 as organisations become even more aware of the gaps that legacy architectures such as VPNs pose to their security posture.
Cybersecurity in healthcare is a matter of life and death
The health sector is playing a key role in the fight against COVID-19 through all the measures to combat the spread of the virus, greater efforts in R&D for tests, treatments and vaccines, implementation of new technologies, etc. However, with the growing dependence on health technology and virtual platforms, and the chaos caused by the pandemic, cyber security has been pushed into the background, and cyber security threats continue to increase exponentially in the sector.
Cybersecurity in healthcare is critical given the large amount of personal and confidential information often found in patients’ medical records, and the problems that can result from ransomware or phishing attacks that can disrupt their ability to provide care to patients.
For example, in early 2020, a patient was unable to receive life-saving treatment because cyber criminals disabled all computer systems at Düsseldorg University Hospital with ransomware. This caused the patient to lose his life. In addition, there have also been recent cyber attacks against the COVID-19 vaccine development facilities in the UK and the USA.
Knowing that cyber-attacks can have fatal consequences and that many healthcare organisations may not have adequate cyber-security controls, attackers are in a prime position to launch all kinds of threats.
This trend will continue to grow in 2021 as more health care systems adopt the use of technology.
Financial organizations should be very careful
Financial services organisations and other businesses that are responsible for the security of consumers’ financial data should remain vigilant in their cyber security efforts during 2021. The high value of financial data makes them a lucrative target for cybercriminals.
It is true that financial services companies do not suffer cyber attacks as often as other industries. However, when they do occur and are attacked, these incidents tend to be much more significant and damaging than those experienced by companies in other industries.
With the projected increase in new technologies, such as 5G, during 2021, cybercriminals are likely to improve the sophistication of their attacks on financial institutions. It is therefore imperative that they take a proactive approach to data protection.
The persistence and growth of ransomware
With ransomware attacks, cyber criminals take control of databases and block user access. They then request money or a ransom before providing access to the organisation.
The sad reality of COVID-19 is the ever-increasing unemployment around the world. This has created concern about the distribution of wealth, and cybercriminals are doing everything they can to harm corporate entities through cyber attacks. Ransomware attacks that involve holding a company’s database in exchange for crypto-currency or some other form of financial compensation are becoming all too common in 2020.
In addition, it is now being seen that cyber criminals are blocking the most sensitive and confidential data and architectures that a company may have, leading to requests for much higher ransom amounts. Ransoms have already reached tens of millions of dollars, and it is expected that this increase in the amount demanded will be a trend that is likely to continue or even worsen.
While many organisations pay ransoms and regain access to their data, they often forget that cyber criminals still have their data. Ransomware operators are becoming increasingly aggressive, and by 2021 it is expected that criminals will use this retained data in other ways as they digest the content. This could include coming back with more financial demands or publicly exposing an organisation.
By 2021, any organisation must be prepared for a ransomware attack. This means ensuring that networks are segmented, that there is a real plan in place and that practical exercises have been conducted with company leaders and staff so that everyone is ready to take optimal action.
Organizations will be targeted and compromised, so prevention and recovery strategies are crucial.
Integration of AI
As cyber attacks continue to grow in intensity and frequency, Artificial Intelligence is ready to help under-resourced security teams stay ahead of the game. In fact, according to market estimates, AI in cybersecurity is projected to grow from $8.8 billion in 2019 to $38.2 billion by 2026 at a compound annual rate of 23.3%.
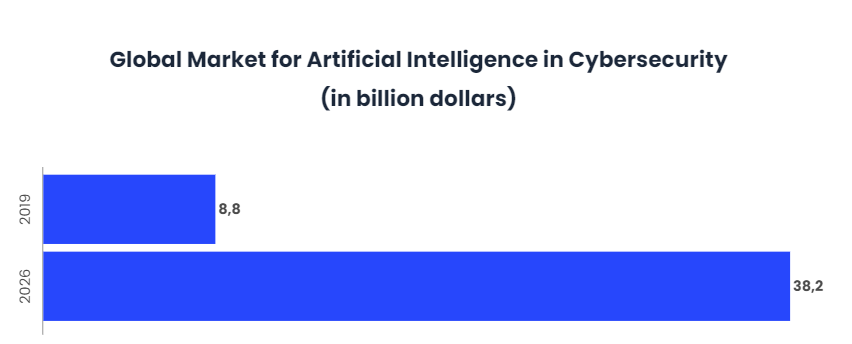
By analysing large amounts of both structured and unstructured data, AI provides threat intelligence, reducing the time it takes the security team to make critical decisions and respond to address those threats.
5G Implementation
It is estimated that 5G will cover almost 40% of the world by 2024 with data transfer speeds of up to 10 GB/s. Without doubt, 5G technology is a great example of progressive technology available to users around the world.
However, while this technology will make life easier, compromising and leveraging new 5G-enabled devices will also open the door for new cyber security threats to emerge.
With high-speed data transfers, cyber criminals will have the ability to infect data packets and conduct corporate espionage without companies noticing. That will happen until companies are aware and change their approach to stop these attempted violations.
Much higher levels of security and monitoring will be required once 5G becomes the standard form of cloud-based data transfer and communication.
Automation in cybersecurity: is it the solution?
One thing is clear from all this, and that is that cybercriminals will continue to improve their techniques for entering company databases, so companies will also have to improve their detection tools.
If you look closely at the challenges of cyber security, you can see that traditional methods are not strong enough to combat cyber attacks. The number of cyber attacks is exponentially greater than threat detection tools can identify, and it is not possible to respond manually to the enormous number of alerts that appear every day. Investigations are too long, resulting in massive data breaches, and current protection measures cannot keep up with the pace of attack propagation.
This is because, according to the data, the average time it takes to identify and contain a breach is 280 days, which costs an average of $3.86 million. And this is where automation in cyber security can help.
Cybersecurity automation eliminates the need to manually perform tasks that are repetitive. It can therefore provide better results, at a faster pace, and can operate more efficiently. And this is why 88% of cybersecurity professionals believe that automation will make their work much easier.
- Automation of threat correlation: Continuous security testing helps detect new malware variants, Trojans and ransomware. The automation of the threat correlation plays an important role in activating proactive protection through machine learning and automation. This solution provides defence not only against known but also against unknown threats.
- Real-time prevention: Real-time prevention places an organisation in a privileged position to defend itself from the next cyber attack.
- Automated Penetration Testing: Penetration testing is an in-depth assessment of a company’s cyber security that is performed manually by an operator or by a team. This test can be used to access the target network and identify internal problems in the network. However, the entire process involves many repetitive tasks that increase processing and analysis time. The automation of the penetration test automates the repetitive actions, which increases and improves the performance. Automated penetration testing tools allow the person being tested to identify security control breaches much more quickly, as well as to analyse and define which techniques were used by the cybercriminals to escape other controls.
- Automation of vulnerability scanning: Vulnerability scanning is an automated process for searching for vulnerabilities. This process should not be confused with penetration testing, as the aim here is to discover regular security flaws, such as the use of weak passwords, by means of an external and internal scan. This makes it possible to better detect all potential vulnerabilities.
- Automation of security patch management: Software companies release patches (code) created to correct vulnerabilities, but sometimes this patch does not reach the operating system, which can result in a cyber security breach. If this process were automated, the code needed to keep the system secure could be located, tested and applied. This process would work regardless of whether the software company’s patch is installed or not.
- Automation of HTTP/HTTPS traffic logs: In order to detect malicious activity, it is also necessary to study the HTTP/HTTPS traffic logs. This process is long, tedious and cannot be done manually, so its automation, through a Machine-Learning algorithm, is perfect. These ML algorithms analyse both current and historical traffic logs to identify possible malware segregated on a channel. In addition, if detected, this malware is downloaded into a sandbox environment for review.
Automation in Cybersecurity helps to predict potential risks and take action more effectively and quickly. In addition, by automating many of the repetitive tasks, human participation is minimised, freeing workers from these tasks and allowing them to focus on more important and weighty tasks.
With the growth in the number of cyber attacks and the increasing accuracy of cyber criminals in gaining access to a system, cyber security automation is a safe solution to prevent cyber attacks and data breaches.
Conclusions
With the arrival of the COVID-19, people’s lives have moved online, both at work and in person, and the digital transformation has accelerated. Technology is helping to maintain a certain social and emotional well-being, and for many companies it has helped to stay afloat. However, this new reality has also led to an increase in the number of cyber-attacks.
Companies had to adopt teleworking overnight, creating certain cracks in their security shields as a result of ignorance and haste. This, and social fear, is what the cybercriminals, who also rushed to adjust their tactics, have taken advantage of to continually launch cyberattacks.
As cyber attacks increase and new cybersecurity trends continue to emerge, companies must take a proactive IT security stance to keep their businesses safe. They must become more agile, more flexible and collaborative as they strive to protect their critical assets. To achieve this, cybersecurity automation can be a very good option.
.jpg?width=352&name=alex-robert-Xpt4_HgZSjw-unsplash%20(1).jpg)

