The new Cybersecurity Grid architecture

With the rise of remote working in the wake of the pandemic, cyber threats have increased significantly, so companies have had to adapt their operations to ensure scalable and flexible cyber security access control.
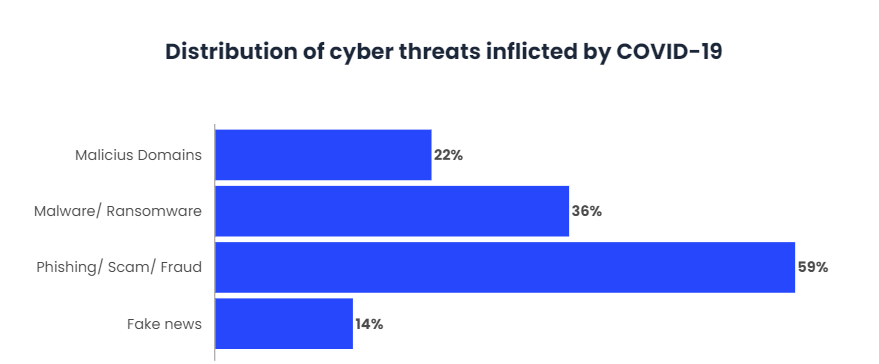
With the rise of remote working in the wake of the pandemic, the threats are increasing. At this point, new methods of protecting a company’s infrastructure have emerged, with cyber-security meshes to ensure protection outside the traditional security perimeter. The aim of this type of security is to ensure the protection of each access point, effectively managing it through a centralised centre of authority.
Hackers are increasingly using cloud-based ransomware as remote needs grow. In other words, a company’s users increasingly need identification permissions that lead to more cyber-attacks in the cloud. Hackers look for weaknesses in applications and infrastructure as companies migrate to the cloud.
The increase in attacks with cloud migration is mainly due to the fact that scalability is sometimes difficult to track in the infrastructure and this creates new attack opportunities. Therefore, by making use of new tools such as cyber security meshes, any digital asset located in any location can be protected, creating greater protection against new threats. cyber threats have increased considerably, so companies have had to adapt their operations to ensure scalable and flexible cyber security access control.
What is a cybersecurity mesh?
Cybersecurity meshes are defined as a distributed architectural approach to scalable and flexible cybersecurity control. Digital assets currently reside in applications, IoT, containers or in the cloud, and through cyber security grids a security perimeter can be defined around the identity of each object.
This creates a modular and responsive security approach to the centralisation of application orchestration and distribution. Traditional perimeter protection must therefore evolve to meet today’s needs in order to become more meaningful.
Cybersecurity meshes mean that networks do not have a joint boundary, but instead build perimeter security around each user, so that assets can be accessed from anywhere and identification policies are enforced via the cloud on the asset itself rather than on a device.
A cyber security mesh thus requires the design and implementation of an IT infrastructure around individual nodes, establishing individual perimeters around each access point.
It also brings great benefits in centralising security policies and ensuring that the application is more distributed. In addition, the cyber security mesh refers to the integration of security in a horizontal distributed approach to a network rather than a traditional all-encompassing vertical approach.
In parallel, it should be noted that cyber security meshes involve a wider network of nodes than Confidential Computing, which relates more to security around data processing.
Businesses should use cyber-security meshes
This new architecture provides companies with greater security and protection that extends to where employees and company assets are located. This means that if critical infrastructure is located outside the traditional security perimeter, these can be critical access points to documentation belonging to the company.
Therefore, the company’s security infrastructure must be comprehensive and agile to cover any employee working remotely, and this can only be achieved by decoupling decisions and implementing new cyber security policies.
Consequently, this involves a new line of security monitoring, where the traditional boundaries that were imposed on each company must be redrawn. Therefore, access to information is guaranteed throughout the network no matter where the physical employee is located.
It is therefore necessary for companies to have an appropriate development team in place to establish a security mesh for their projects from the outset of project planning, ensuring that all necessary measures are in place to prevent and control cybersecurity threats at all access points.
For any company implementing this architecture, user and network identification will require continuous evolution. In many cases, VPN servers are used to hide digital identity and make it more difficult for attacks to infiltrate the network. For example, Smartz Solutions authentication and Profile Anywhere take care of managing and administering devices, so that they ensure that the linked device is the correct one and its data is protected.
As a result, the security mesh ensures complete security when accessing digital assets regardless of where the access takes place. Identification becomes the security perimeter by decoupling centralised applications from access to information, all thanks to a cloud-based model.
Benefits
The benefits of using cyber security meshes as an architectural approach to protecting digital assets are diverse and useful:
- A cyber security mesh is capable of supporting a higher volume of requests through an Identity and Access Management (IAM) system than traditional cyber security. Meshes support more than 50% of requests and enable a unified and adaptive access management model. Enterprises can therefore have more scalable and secure cyber security for different access points and asset control than if they were working with traditional perimeter security.
- Managed security service providers provide companies with the quality resources needed to plan and implement end-to-end IAM solutions.
- Meshes can address common weaknesses in workforce identity lifecycle processes by adding testing tools for this purpose. In many companies, more robust enrolment and recovery processes are really needed because of the high volume of remote interactions, which does not allow for clear identification between regular users and cyber attackers.
- The decentralised approach implied by cybersecurity meshes and Blockchain technology ensures excellent privacy and enables the validation of information requests because it provides the requester with the minimum amount of information required.
- During the pandemic, with the massive mobilisation of remote working, it was discovered that there are many ways in which identity bias can occur. The use of cybersecurity meshes minimises demographic bias in identity verification.
Conclusions
As mentioned above, the massive advent of remote working has made it more difficult to identify between in-house users and attackers. Thus, the idea of the new architecture of cyber security meshes has emerged. These serve to provide a modular and trusted approach to any network, ensuring that each node has its own perimeter rather than a global perimeter as in traditional cyber security.
Thus, IT teams can properly track the access levels of a network and prevent attackers from looking for weaknesses in nodes to gain access to broader network information.
Among the benefits provided by this approach are that meshes enable a greater number of IAM requests than traditional approaches, improve the planning and implementation of end-to-end solutions, address common weaknesses in workforce identity lifecycle processes, ensure greater privacy, and minimise demographic bias in the face of increased remote working.


