The idea of protecting servers is reinforced

At the beginning of March 2021, several cybersecurity researchers have detected a ransomware that exploits different vulnerabilities in Microsoft Exchange servers. These vulnerabilities are known as zero-day, as they are unknown, and are: CVE-2021-26855, CVE-2021-26857, CVE-2021-26858 and CVE-2021-27065.
DearCry is the nickname for the ransomware that disables computer systems in order to demand a ransom for them. The attack is initiated by exploiting a server-side request forgery vulnerability to steal the contents of the user’s mailbox. Attackers can take over servers without knowing account credentials, because flaws can be chained together to create a remote code execution exploit. Preventing the attack by patching is straightforward, but systems already affected will not be easy to fix.
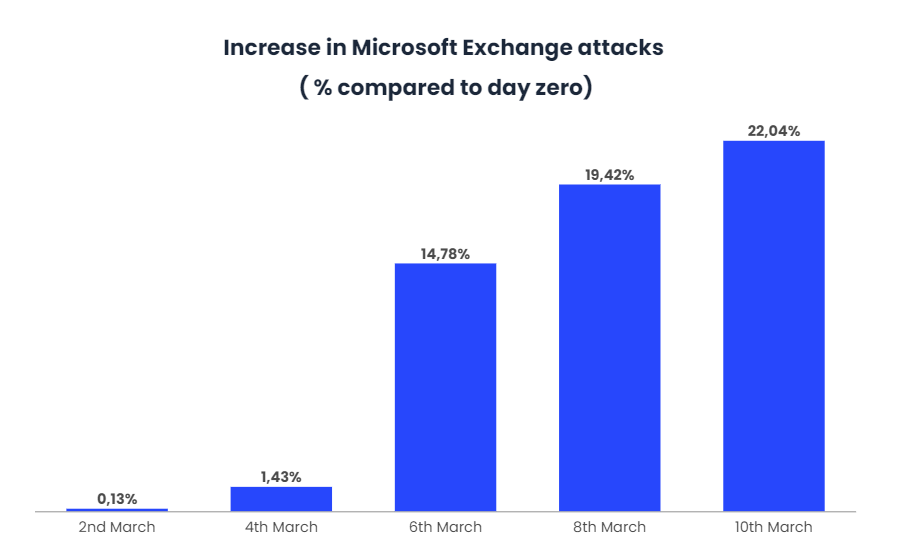
Around 30,000 companies in the US have been affected and attacked by the ransomware, including industrial companies, law firms and infectious disease research laboratories. Turkey, the US and Italy have been the most affected countries so far, with 17% of attacks on the public and military sector and 14% on the industrial sector.
The vulnerabilities
Initially, four vulnerabilities have been detected in Microsoft Exchange servers, these only target on-premises servers. Cloud servers are therefore not affected by these system flaws.
The initial information required by the attacker is the server where the Exchange software is running and the account he wants to steal (CVE-2021-26855). Using a second exploit chained to the first, it allows remote code execution on the server (CVE-2021-27065). The third vulnerability, which is also part of this second chained exploit, allows a new file to be written to any path on the attacked server (CVE-2021-26858). The last flaw allows SYSTEM code to be executed after attacking the deserialisation vulnerability in the unified messaging service (CVE-2021-26857).
- CVE-2021-26855: This vulnerability is used for a server-side request forgery attack resulting in remote code execution.
- CVE-2021-26857: this second vulnerability is used to execute arbitrary code from part of the system. You need to have administrator permissions or have exploited the previous vulnerability.
- CVE-2021-26858 and CVE-2021-27065: these last two code identifiers, which refer to the latest vulnerabilities, are used by attackers to overwrite server files.
Most of the attacks seen so far use all the vulnerabilities together to carry out the attack, but Microsoft claims that stolen credentials can be used to authenticate without using CVE-2021-26855.
Response measures
The recommended prevention measures are, first of all, to identify and apply the necessary patches to the system, using the updates issued by Microsoft. So far, the vulnerable versions of Exchange Server are 2013, 2016 and 2019. Thus, it makes an update recommendation for all servers, mainly those that are connected to the internet.
Secondly, it is recommended to use the temporary alternatives offered by Microsoft when patches cannot be used. As long as SSL decryption is enabled for Exchange Server data traffic, next generation firewalls protect against these vulnerabilities, as is the case with Palo Alto Networks (NGFW).
To protect against this second vulnerability, you can restrict access to the system to untrusted users through a VPN or by using a firewall to limit access to different IPs. It should be noted that this process will only protect against the initiation of the attack.
Third, a search for indicators of compromise can be performed by using Microsoft’s PowerShell script. In other words, you should look for whether the organisation has already been compromised, as patching the system does not eliminate malware that is already in place.
Through the Powershell and Nmap scripts that Microsoft has developed to check Exchange servers, indicators of compromise of exploits can be detected. In addition, the Agency for Security and Infrastructure and Cybersecurity has also described a list of techniques and procedures (TTP) to protect servers.
Ultimately, carrying out all these measures will prevent any system from being compromised again in the future. Offline updates are essential to keep servers secure.
Access to confidential information has been totally compromised, as well as corporate emails which can lead to phishing attacks. The first phase can be stopped by limiting connections from outside the corporate network, but this type of protection is useless if the attackers are already inside the server.
How to protect the server?
If you have not yet suffered an attack, protecting the server is essential, even if there are no known threats. There are different ways to protect systems, described below:
- Panda Adaptive Defense 360
Adaptive Defence 360 is an EPP solution, which provides simple, centralised security, with real-time remediation and reporting, as well as web filtering and monitoring. For this case of attack Defense 360 has powershell payload detections. In addition, it performs continuous web access monitoring.
It also automates the detection and response to any threat whether it is phishing, ransomware or in-memory exploits inside and outside the corporate server. This defence system is very appropriate because most attacks are caused by known vulnerabilities, with very few cases of security breaches of unknown vulnerabilities, commonly known as zero-day attacks.
Furthermore, Panda offers the Panda Patch Management system to deploy patches and updates for operating systems and third-party applications.
Therefore, Panda Adaptive Defense 360 is characterised by:
- Provide real-time endpoint visibility, patches and pending updates.
- Prioritise updates to operating systems and applications in a way that monitors system and third-party applications in real time.
- Reduces the vulnerability attack surface in order to prevent incidents by pre-empting the exploitation of weaknesses.
- After detecting an attack, it contains it and mitigates it by means of patches, minimising response time.
- IPS
The function of IPS is to exercise access control on a network to protect systems from attacks. It was developed in order to analyse the data and information of the attack in order to act accordingly, so that it is stopped as it is being executed. In the particular case of the attack on Microsoft Exchange, Firefox IPS blocks the first stage of the attack.
- Gateaway Antivirus
This antivirus allows applications to check files for different viruses while providing a SOAP-based virus detection web service. Gateaway has different paths to detect and block the webshells used in this latest massive attack.
- ATP Blocker
For example, WatchGuard APT Blocker performs an analysis to determine if a file is malicious, identifying and sending these files to a sandbox in the cloud where it simulates physical hardware. It is then in the cloud where the code is executed and analysed to detect threats, if it is detected that it is a malicious file APT Blocker blocks and ensures that all digital files remain secure. In other words, this system is able to detect malicious backdoors.
Conclusions
This analysis describes what has happened to Microsoft Exchange over the past month, but the aim is to make all companies, whether large or small, aware that it is critical to protect their computers and servers, whether through anti-virus, updates or patches, but the combination of these three will provide key protection against sensitive data theft, hijacking and phishing payments.
In the case of Microsoft Exchange, it has released indicators of compromise along with the publication of Powershell scripts and various Github tools to help identify threats and attacks against these vulnerabilities. A number of IT companies have contributed to publishing information on these threats so that they can be managed and dealt with by companies that do not have sufficient tools.


