Entropy is not always effective in the face of a cyberattack

In computing, entropy is a tangible resource. The term describes the random information collected by an operating system to generate cryptographic keys used to encrypt information. As entropy increases, both in quality and quantity, keys become more difficult to decipher, and encryption improves.
Traditional computer systems can generate inventories of the physical world by tracking users’ movement with the mouse, for example, providing all the entropy needed to develop complicated cryptographic keys. However, these sources begin to run out when computing moves out of the physical world into the cloud.
According to the latest reports, the protection mechanisms currently in place are not adequate to address today’s threats. Sixty-six percent of violations take months or years to discover. Yet 84% of these attacks only took a few hours or less to be perpetrated.
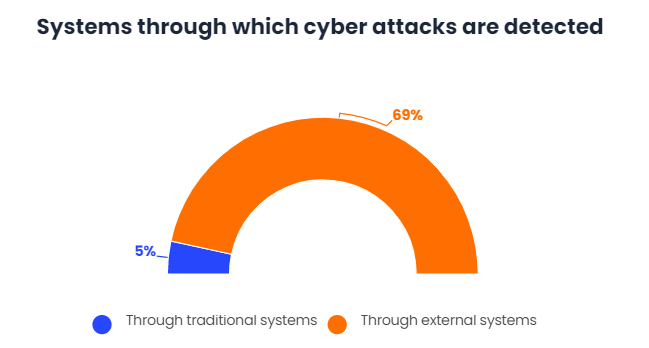
In addition, only 5% of these breaches can be detected by traditional intrusion detection systems, while 69% are detected by external parties.
Is entropy found in all systems?
Although cloud devices now cover every conceivable field, from IoT sensors to integrated systems, they do not have a natural source of entropy. Mainly because they are largely unattached to real users. Many of these devices operate autonomously, without human intervention.
Previously, developers applied the same collection techniques used in software-based entropy, assuming it could generate adequate entropy. However, that option was rejected after an investigation of cryptographic keys inside firewalls and routers, where multiple duplicate keys were discovered, offering criminals an easy way to avoid encryption.
These duplicates occurred mainly because there was not enough random information available to generate unique keys. As more computing resources move to the cloud, insufficient entropy will become an important security responsibility. Which means that the future of encryption, security and online privacy depend on finding more sources.
Understanding the scope of this problem, the National Institute of Science and Technology has recommended creating new entropy sources adapted to today’s computing environments, Entropy as a service (Eaas).
Entropy as a Service
NIST recommends entropy as a service to provide strong cryptographic keys for cloud-based applications and integrated IoT devices. An entropy server as a service targets virtual machines and containers that cannot properly generate secure cryptographic keys.
The EaaS relies on ring oscillators and quantum devices to generate endless amounts of entropy and truly random features. Developers can use this data and use it in new applications or perform cybersecurity tests.
This is an asset for any developer who lacks numerous entropy sources. Instead of searching for data that simply isn’t there, developers can collect exactly the amount they need. Removing this obstacle provides both accelerated development times and improved cybersecurity.
The benefits continue beyond development:
- Applications must be continually updated with entropy to stay ahead of predatory hackers. EaaS provides a constant supply of new information, free of patterns that hackers can predict and exploit. It’s a way to stay one step ahead of tomorrow’s cyber security threats.
- Enterprises can use EaaS outside of a development context. Comparison of keys generated through software-based resources with a new entropy reveals whether those keys are truly secure. Instead of assuming that cryptography is secure, EaaS tests it objectively.
The companies supplying EaaS
Several companies are already involved with EaaS, supplying entropy and refining how it is collected. A decade ago, no one cared about the lack of entropy. Now, however, this problem puts the digital future at risk. Entropy as a service is still maturing, but it will soon become a standard development tool that is indispensable for Internet security.
For example, a company specializing in cryptography, in 2017 began to provide a free service to use with free software or with paid versions that provide entropy in perpetuity (depending on consumption). Thanks to this service, random data is collected through a proprietary generator which supplies all other areas, from operating systems to virtual machines.
The objective of these services is none other than to generate less predictable cryptographic keys, thanks to the possibility of analyzing a great multitude of sources, and to improve the security of the devices.
The failure of the Bluetooth connection
Until now, only the virtues of entropy to improve device security have been mentioned, however, it can also present vulnerabilities.
Recently cyber security researchers have discovered an error that affects almost all devices that use the Bluetooth wireless connectivity protocol.
The vulnerability, named CVE-2019-9506, resides in the way the ‘encryption key protocol’ allows two Bluetooth BR / EDR devices to choose an entropy value for the encryption keys while pairing to secure their connection.
This failure could allow a remote attacker to trick two specific devices into agreeing on an encryption key with only 1 byte (8 bits) of entropy, making it easier for them to intercept, monitor or manipulate Bluetooth encrypted traffic between the paired devices.
From a security point of view, the central specification of the Bluetooth protocol supports encryption keys with entropy between 1 and 16 bytes (where the higher value means more security).
However, experts believe that entropy negotiation, which devices perform through the Link Manager Protocol (LMP), is neither encrypted nor authenticated, and can be hijacked or manipulated.
Once decrypted, the attacker can passively capture encrypted messages that are transmitted through Bluetooth traffic, decrypt the text, and inject valid cipher text, all in real time and stealthily.
In addition to this, it is also important to keep in mind that for an attack to be successful a number of situations must occur:
- Both Bluetooth devices must establish a BR / EDR connection.
- Both Bluetooth devices must be vulnerable to this defect.
- The attacker should be able to block direct transmissions between devices while pairing.
- The attack must be performed during negotiation or renegotiation of a paired device connection; existing sessions cannot be attacked.
In the face of this event, to mitigate the KNOB attack, it is recommended that device manufacturers and software vendors apply a minimum encryption key length of 7 bytes for BR / EDR connections.
To repair this vulnerability, several affected vendors such as Apple, Google or Microsoft have already begun to release security updates for their operating systems, especially for iOS and Android smartphones.
Conclusions
Business cybersecurity is one of the essential elements to be taken into account when carrying out a successful business strategy. There are currently a multitude of attacks, perpetuated from all possible angles.
Therefore, by intelligently using deceptive techniques, such as creating passwords through entropy, defenders of the system can confuse attackers, thus improving their defense capabilities over time.
However, all possible options must be considered, entropy is now a good way to judge how difficult it would be to force a password by brute force. However, a high entropy does not mean (and never) will mean an invincible password. Therefore, taking the measures suggested by the providers to solve the possible vulnerabilities that arise over time is indispensable.


