Beginning a new era for passwords?

Questioning the security of passwords in the face of a cyberattack is not a new issue, and that is that protecting oneself in the digital world is everyone’s responsibility. Passwords were first introduced into the computer world in the 1960s, probably by the same team at the Massachusetts Institute of Technology that created e-mail, instant messaging, and file sharing, and despite all the years that have passed, their effectiveness is still surprising, though increasingly contested.
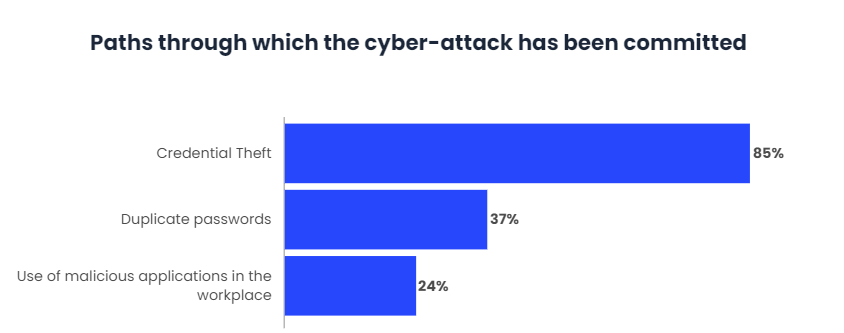
For example, a recent survey found that 74% of all infractions involved access to a privileged account. This means that hackers most of the time don’t force their way in, but rather have the correct passwords to enter the device through its “front door”.
Is it necessary to abandon passwords?
In 2018, Microsoft declared the “end of the password era” at its Ignite Conference. Between phishing and brute force attacks, malware exfiltration attacks and social engineering, people have many concerns about commonly used passwords.
Devices using new versions of passwords are improving their security. So using the term “password” is not entirely correct when thinking about privacy and authentication in the future.
These new “passwords” include biometrics, with all its variables, and two-factor authentication (also known as “2FA” and “two-step verification”).
Biometrics is starting to come true.
- Fingerprints are now commonly used in banking applications, credit cards and many smart devices.
- Facial recognition has begun to solve initial problems and is now 95% more accurate according to the latest studies.
- Retina scanning has the lowest error rate of all these systems, it has begun to move away from only physical access uses and other authentication processes.
- Voice recognition is taking off, especially as a key tool for smart home devices, allowing different preferences and security settings for different users.
- Palm vein recognition has been used in the healthcare sector for years and is currently being considered for some retail payment systems.
Two-factor authentication (also known as “2FA” and “two-step verification”)
2FA is a technology that adds an additional layer of security to passwords. As the name implies, these passwords require two different blocks of information.
In general, authentication is required when sharing or activating something that only the user knows (for example, a password or security question), something that the user has (for example, a mobile phone with an authentication application or a similar small security device), or something that is a part of the user (for example, a fingerprint or face).
New ideas, new options
Without detracting from these technologies, the latest reports published on device security make clear the weakness of passwords and therefore the vulnerability of the data stored in them.
- Ninety per cent of security professionals have witnessed security incidents resulting from credential theft.
- 86% of vice presidents would abandon password authentication if they could.
- Mobile devices protected by biometric authentication methods present the best option for replacing passwords.
- There is a direct correlation between the number of times a user is authenticated and the number of user access problems that need to be addressed.
Some of the above options may be the main element that secures the devices. However, they are not the definitive ones, so other security options have appeared that could surpass all this.
It is not known exactly what digital security will look like in ten years, or even five years, but along with two-factor authentication and biometric possibilities, there are some other possibilities as well.
- Authentication of the beat signal:
This type of identification has been perceived as less intrusive than fingerprints, retinas and other biometric data. The electrocardiographic signals produced by each individual’s heart are truly unique, and their use as access codes or as a means of authentication could be as simple as tracking these rhythms on an intelligent watch or other portable device.
The Pentagon, at the request of U.S. Special Forces, has created a device capable of identifying people without seeing their faces, detecting the unique cardiac signature with an infrared laser. At the moment it works up to 200 meters away, but this figure could be amplified with a better laser.
It is a technology that can achieve an accuracy of more than 95% in good conditions, and that could be improved even more.
- Brain waves:
One of the latest technologies being developed, uses as an access code measure the brain structure of an individual, its brain waves. This type of password stands out because they are authentication measures are difficult to duplicate, although they can actually be updated if necessary.
Brainwave passwords record your reactions to a stimulus, like an image. Those stimulated brain waves would be your password. If, in any case, the data behind these brain waves were compromised, you could simply reset the password with another stimulus, which would produce a different reaction.
- Zero Login:
This method uses behavioral characteristics, including location, writing patterns, touch pressure on the phone screen, proximity to other devices, such as a smart watch, headset, or even a car, and other unique identifiers.
Users of any application tend to repeat patterns of behavior, this technology analyzes those movements and when the user performs them already has access.
Conclusions
Passwords are one of the biggest challenges of the digital age. They have been since their first use in the 1960s, and surely will be in the coming years.
New technology will change passwords and authentication as we know it, from personal email communications to the shopping experience.
However, it is important for users to be aware of all possible protection options as hackers would find ingenious ways to steal passwords and privileged access credentials instead of spending time trying to hack into an organization’s systems.
Relying only on traditional passwords to protect devices makes them Zero Trust’s weakest defense. The time has come to eliminate passwords as they are known, for more effective approaches to security and authentication.


